- cross-posted to:
- bitwarden@discuss.tchncs.de
- privacyguides@lemmy.one
- cross-posted to:
- bitwarden@discuss.tchncs.de
- privacyguides@lemmy.one
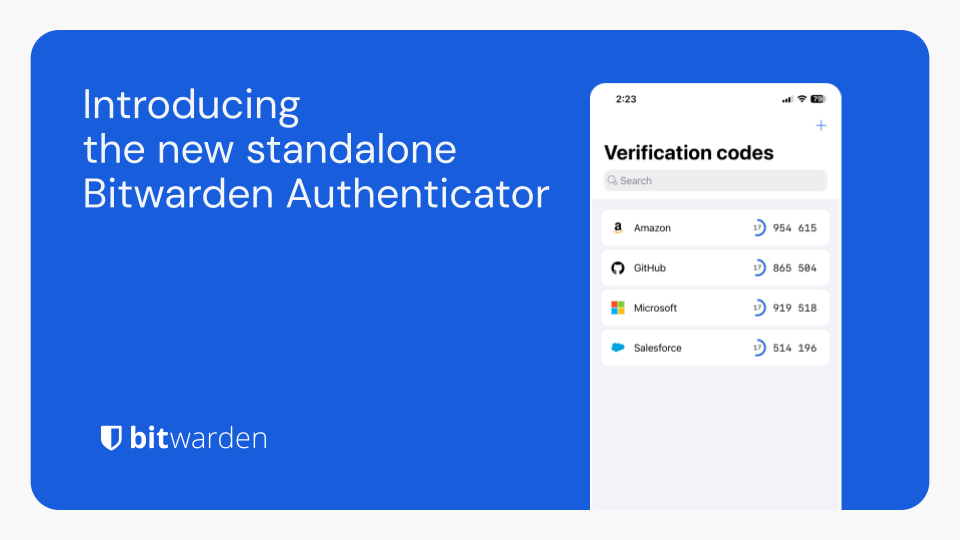
Bitwarden Authenticator is a standalone app that is available for everyone, even non-Bitwarden customers.
In its current release, Bitwarden Authenticator generates time-based one-time passwords (TOTP) for users who want to add an extra layer of 2FA security to their logins.
There is a comprehensive roadmap planned with additional functionality.
Available for iOS and Android


I used to use Aegis, but after setting up my own vaultwarden, I use the normal bitwarden app/plugin on all my systems for passwords and TOTP.
The advantages are that I don’t need my phone to login, the keys are synced and backuped in the encrypted vaultwarden database, which I can then handle with normal server backup tools. It still works offline, because bitwarden app caches the password.
This is IMO much more convenient and secure (in a way that loosing access to a device doesn’t shut you out, and you don’t need to trust third parties) then most other solutions.
Even if I hosted my own BitWarden vault, I wouldn’t put my passwords and 2 factor tokens in the same place because it’s eliminating the benefits that 2 factor provides if someone somehow manages to get into my vault.
2 factor came into our life because people were using same passwords everywhere. With unique passwords, which are easy with password managers, it’s rarely needed.
That may have been part of the reason, but the theory behind MFA is that there are 3 primary ways to authenticate who you are: what you know (password), what you have (secure one time password generator or hardware token), and what you are (biometrics). Password managers and digital one time password generators have kind of blurred the lines between passwords and one time passwords, but you’re raising your risk a bit if you put them in the same place.
With unique passwords, the attack surface just changes. Instead of attacking the passwords, attackers attack the password managers. LastPass, Okta, and Passwordstate each had breaches, and the first two are quite popular.
That doesn’t mean Bitwarden is at risk (not sure if it has been targeted), it just means that attackers are finding success going after password managers, so they could go after Bitwarden. Maybe they’ll sneak in an xz-style bug that’ll allow attackers to steal credentials en-route, idk.
So it’s a matter of good/better/best:
The overhead from using a separate 2FA app is pretty low, just make sure it encrypts your keys and you trust it (FOSS is a good indicator of trust).
There is not much difference between having two apps (password manager and authenticator app) or one app, that does both on the same device.
So, if you want more security, then you have to deal with a hardware token and never with a authenticator app. But then if you loose your token, then you have trouble.
I don’t think it caches the password. Rather a decryption key is derived from your password and is used to unlock the encrypted blob.
What I meant is that is caches the password database for offline use.